We’ve all had those instances when we can’t remember our login to a website due to having so many IDs and passwords. However, this can be more than just a minor irritant for medical staff in hospitals and other care facilities. Many clinical users log into 6-8 different systems during their shift, and need to be able to quickly log in, get their work done, and move on. The solution that has become commonplace in Healthcare IT is called Single Sign-On, or SSO. It is based on the idea that users should be able to provide their User ID and password on one system infrequently, then have expedited access to other systems for a period of time.
There are many variations on how SSO is implemented, and some debate if it really should be called “Single-Sign-On”. To understand what I mean, let’s look at some of the models:
User ID And Password
In this model, users will log into any PC on the hospital network with their User ID and password, once per day. A server and software will authenticate them, many times using Microsoft’s Active Directory technology. That configuration maps the users’ login credentials to multiple other systems in the hospital or other location, securely giving them access to all of those other applications. Those applications may be displayed as links on the desktops of all PCs, or using some other software tool, such as a “launch bar” displayed at the top of all PC workstations.
ID Card Authentication
This model is very popular at hospitals. As in the previous example, users will log into the network at the beginning of their day using their full User ID and password. Software has already been configured to link their badge to their network ID, so that they can tap or swipe their ID badge much like today’s hotel room keys. That auto-authentication expires after several hours to protect against the risk of the employee losing their badge.
Biometric Authentication
In this model, the User ID and password authentication from the first example may or may not apply. The user has previously recorded their fingerprint as ID, and now they simply touch a fingerprint reader to gain access. While this method has always appeared a bit creepy and “Big-Brother’ish” to a lot of folks, it is slowly gaining acceptance in many places.
Proximity Cards
I saw this for myself at a recent conference. In this setup, users wear a tiny detector that just fastens to their badge. After performing the requisite daily login to verify identity, a small receiver at the workstations detect the location of the user when they are about 2 feet away. They are then given access until they step a couple of feet outside the detection range. I’m not sure how popular this method is, and if it’s subject to interference. If anyone has seen this in action, feel free to email me or contact me on social media.
SSO Diagram
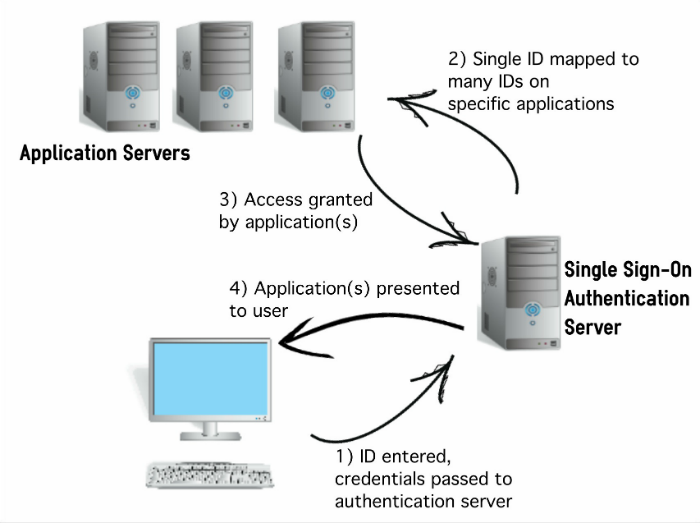
Finally, I wanted to note that there is talk in the tech community that the no-so-distant future might bring a time when User IDs and passwords are not used at all.
Next Up:



